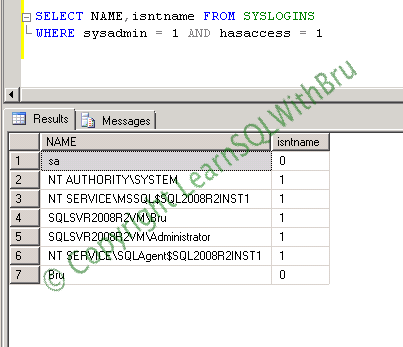
Should we be worried about a read only user? At first look, it looks like, “no we shouldn’t be worried” by a user who has only read access to a database. That is only partially true and on several occasions, I had to explain the people requesting such as access what potential danger, such a read-only user can cause. So I thought it might be a good blog post to publish.
Whenever you come across a read-only user, we assume we are good from the security perspective that it’s ok for this particular user to have a read permissions on the database and there is no harm as that user cannot make any changes to the underlying data. I agree to that statement, but from a point of view other than data security, we will have to recognize that there can be an impact on the performance of SQL Server, on which this database exists.
Consider the case if this read-only user credentials are used in an SSIS package to read a large chunk of data and pushed across to another data destination. When a large number of rows are read from the SQL Server database, that data is first brought into the buffer (memory) of the SQL Server, there by causing any data inside the buffer (that is being actively used) to be flushed off the memory. This might cause a huge impact on the other applications (that read/write to the dbs on this SQL Server). So always keep in mind about this whenever you are creating a read only user. Educate the user who is requesting the read only access about these potential performance impact and let them try to limit their result sets to as minimal as possible..
–Bru Medishetty
Do you like this site? Like our FB page @Facebook.com\LearnSQLWithBru so that, you know when there is a new blog post.